Last weekend was a tidal wave in the IT world: a massive computer attack hit hospitals, large companies and government agencies around the world. WannaCry, this malware collects, encrypts a computer’s data, and asks victims to pay a bitcoin ransom to recover their data.
Fortunately, the Wanna Cry virus would face a major obstacle. It was in his bedroom, at his parents’ home, that Marcus Hutchins, a young British man, would have found by chance the means to stop its propagation for a while at least. The attack was abruptly stopped by a technician from a cyber security company, Kryptos Logic, with the help of Darien Huss from the security firm Proofpoint. The duo discovered that the creator of the malware had designed a kind of “switch” that could be used to prevent the virus from spreading. In practice, the virus is designed to connect automatically to the domain name. If the latter does not respond, it blocks the computer and encrypts the data. If, on the other hand, the domain name responds, then the software is disabled, and that’s what happened when Marcus Hutchins bought the domain name.

Marcus Hutchins – photo:Frank Augstein / AP
The WannaCry Cyber Attack that will make you cry!
WannaCry (“want to cry” in English) has wreaked havoc on the IT world in a very short time. Thisransomware is the cause of what is already considered to be the largest computer attack ever known. According to the latest tally by Europol on Sunday, WannaCry has claimed more than 300,000 victims across 150 countries.
In the United Kingdom, the National Health Service was severely affected, bringing the computer systems of 45 hospitals to a standstill. Some facilities were even forced to postpone surgeries and divert ambulances. In France, the car manufacturer Renault was hit by WannaCry on several of its plants. In Germany, billboards on the Deutsche Bahn rail network carried the virus’ ransom message. In addition, there are reports of disruptions to the banking system as well as to several ministries in Russia, while in the United States, it is the FedEx carrier that says it has been affected. In Spain, mobile phone operator Telefónica has confirmed that it was among the victims of WannaCry. It has also been found in schools, universities and hospitals across Asia.
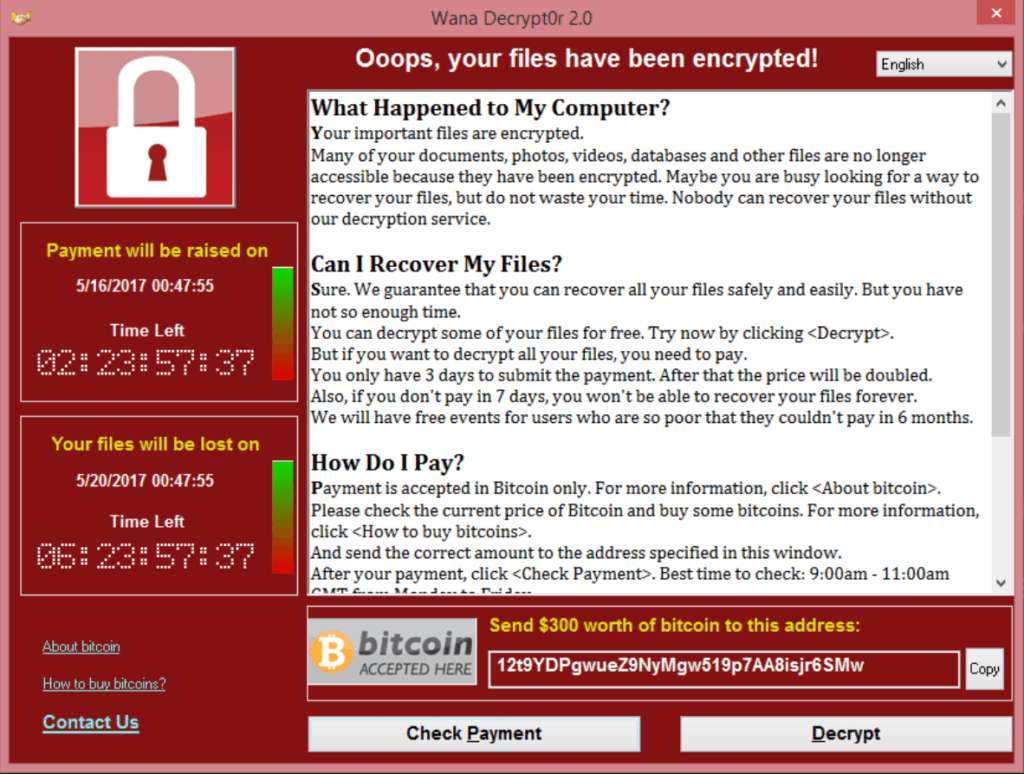
Here is a screenshot of the message that victims of the WannaCry ransomware see on their infected computers. A countdown clock gives them three days to pay the 270 euros in bitcoins before the ransom is doubled. After seven days, the data is deleted. WannaCry, DP
How does it spread?
This ransomware is spread through phishing campaigns, a method of sending millions of emails containing an infected attachment. When a victim opens the document, the virus installs itself on their computer, encrypting the data on the hard drive. To get them back, you have to pay a ransom equivalent to 270 euros payable in bitcoins. The ransom is doubled if not paid within three days. And after seven days, if no payment has been made, the data is deleted. Where WannaCry is particularly formidable is that it can spread across an entire computer network from a single infected computer.

WannaCry: born from a Windows flaw known by the NSA
Yes, the worst part is that it wasn’t a technical error that caused all this chaos, but a human error… A nice, old-fashioned human error. WannaCry thus takes advantage of a security flaw in the Windows operating system that the National Security Agency (NSA), the US intelligence agency, was aware of and used in its electronic surveillance operations under the code name “EternalBlue”.
Last March, Microsoft released a security patch (MS17-010) for all affected Windows versions. Nevertheless, many large companies and administrations have not applied this security patch as a precaution. Indeed, in such a case, IT departments must first test the patches to ensure that there will be no conflict on their network. In April, a group of hackers called The Shadow Brokers released a series of NSA spying tools, including EternalBlue. The cybercriminals then only had to use this information to create the WannaCry ransomware.

@The Intercept
Which computers are vulnerable?
According to the alert issued by CERT-FR, the vulnerable computers are :
- Vulnerable and networked Windows operating systems maintained by the vendor on which the MS17-010 patch has not been installed,
- Outdated and networked vulnerable Windows operating systems (Windows XP, Windows Server 2003, Windows 8, Windows Vista, Windows Server 2008, WES09 and POSReady 2009) on which the KB4012598 patch has not been installed,
- All Windows operating systems on which a user would open the malicious attachment.
In light of the seriousness of the situation, Microsoft has relaunched its security updates for the affected versions of Windows while assuring that Windows 10 users were not targeted by the attack. The main recommendation is to perform these security updates without delay and to be extremely cautious of emails with attachments. In addition, regular data backups to an external storage system and/or cloud service can restore hacked data without having to pay any ransom.

How to protect yourself?
In order to protect yourself against this virus, the Ministry of Technology, Communication and Innovation advises you:
- Update their antivirus software on their computers/laptops or install Windows Defender on their computers if they do not have antivirus software,
- Install the Microsoft patch for the SM15 MS17-010 vulnerability dated March 14, 2017 which can be downloaded here,
- Back up important files to external drives or to the cloud.
The department also advises all computer and laptop users not to :
- Open a suspicious unsolicited email with attachments like “! Read Me! Txt” or .exe,
- Or click on links in suspicious emails or social media posts.

You can also contact the Cert-Mu hotline at 800-2378 to receive advice on digital security. If your computer has already been infected by the ransomware, it is recommended to disconnect the computer from the Internet or network and not to pay the ransom.
For the moment, the identity of the person or persons responsible for this cyber attack is unknown. Wannacry has slowed its spread thanks to users downloading updates to protect their computers. The investigation is proving arduous, as bitcoin payments are impossible to trace. Fortunately, there are several tricks to ensure your digital security. Always be careful, because computers are never risk-free.
Source: futura-sciences.